In the Cloud or On-premise
Security and Audit Solutions for Infor CloudSuite and Lawson S3
Easy-to-Use Software, Powerful Features
Complying with government regulations, industry standards, or corporate quality initiatives can be complex and costly, but failing to measure up to such standards is not an option. The Kinsey Risk Management Suite can help reduce the cost of regulatory compliance, mitigate the risk of compliance failure, and protect company assets.
Not sure which solution is right for you...learn more |
Don't just take our work for it, read what our customers are saying.
"As always thank you! Your tool is invaluable and has saved us so many hours of research and the ultimate tool for Audits!" (December 2017)
Glenn Blackshear | Lawson Security Systems Analyst | UCHealth University of Colorado Hospital
Glenn Blackshear | Lawson Security Systems Analyst | UCHealth University of Colorado Hospital
"We had to pull reports and security user access list for auditors this week while other department teams had to log tickets with the A.D. domain and manually generate reports. We were able to just push a few buttons to generate the reports our auditors needed." (March 2017)
Melissa M. Polich │Sr. Manager Application Development |CVS Health
Melissa M. Polich │Sr. Manager Application Development |CVS Health
|
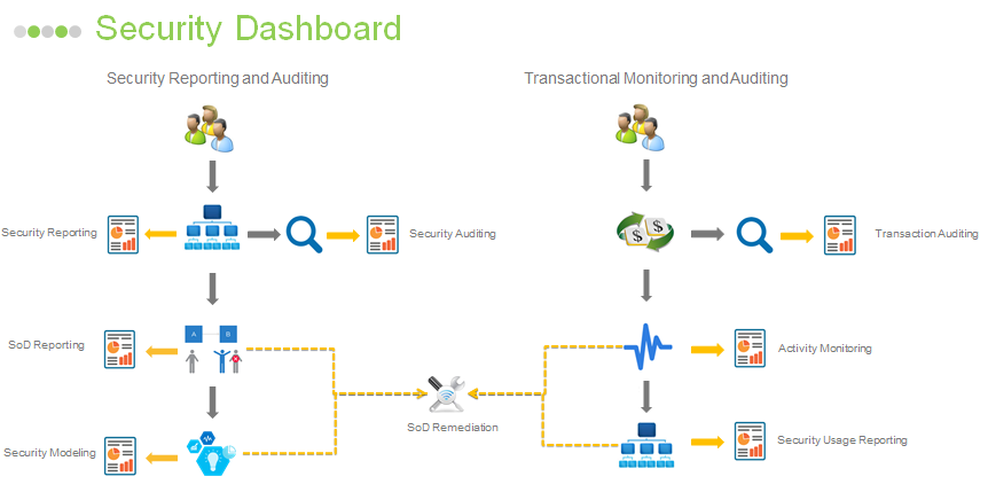
Security Reporting
Easily view, print and export current and historical Lawson Security settings for Users, Roles and Security Classes. Learn More |
Landmark Reporting
Quickly view, print or export your Landmark Actor, Role and Security Class settings including LPL object parameters. Learn More |
Security Auditing
Monitoring changes to your security can be critical. Automatically email reports showing who, when and the changes made to your security. Learn More |
|
Segregation of Duties
Identify Segregation of Duties (SoD) access conflicts and SOX compliance in minutes with reporting capabilities. Learn More |
Activity Monitor
Assess risks more confidently and accelerate remediation time with comprehensive reporting based on 100% of Lawson S3 user data. Learn More |
SoD Remediation
Simply identifying SoD violations within your security model may not be enough. Combine user activity with SoD conflicts to create a remediation strategy. Learn More |
|
Transaction Auditing
Identify risks and accelerate the investigation process by auditing any user transaction in your Lawson S3 application. Learn More |
Security Modeling
Change a user’s role assignment or change a roles application access and test the impact to SoD before assigning. Learn More |
Security Migration
The proven process simplifies the move the from LAUA Security to Lawson Security 9/10 while building a SoD compliant model. Learn More |